More on Marketing

Karo Wanner
3 years ago
This is how I started my Twitter account.
My 12-day results look good.

Twitter seemed for old people and politicians.
I thought the platform would die soon like Facebook.
The platform's growth stalled around 300m users between 2015 and 2019.
In 2020, Twitter grew and now has almost 400m users.
Niharikaa Kaur Sodhi built a business on Twitter while I was away, despite its low popularity.
When I read about the success of Twitter users in the past 2 years, I created an account and a 3-month strategy.
I'll see if it's worth starting Twitter in 2022.
Late or perfect? I'll update you. Track my Twitter growth. You can find me here.
My Twitter Strategy
My Twitter goal is to build a community and recruit members for Mindful Monday.
I believe mindfulness is the only way to solve problems like poverty, inequality, and the climate crisis.
The power of mindfulness is my mission.
Mindful Monday is your weekly reminder to live in the present moment. I send mindfulness tips every Monday.
My Twitter profile promotes Mindful Monday and encourages people to join.
What I paid attention to:
I designed a brand-appropriate header to promote Mindful Monday.
Choose a profile picture. People want to know who you are.
I added my name as I do on Medium, Instagram, and emails. To stand out and be easily recognized, add an emoji if appropriate. Add what you want to be known for, such as Health Coach, Writer, or Newsletter.
People follow successful, trustworthy people. Describe any results you have. This could be views, followers, subscribers, or major news outlets. Create!
Tell readers what they'll get by following you. Can you help?
Add CTA to your profile. Your Twitter account's purpose. Give instructions. I placed my sign-up link next to the CTA to promote Mindful Monday. Josh Spector recommended this. (Thanks! Bonus tip: If you don't want the category to show in your profile, e.g. Entrepreneur, go to edit profile, edit professional profile, and choose 'Other'
Here's my Twitter:

I'm no expert, but I tried. Please share any additional Twitter tips and suggestions in the comments.
To hide your Revue newsletter subscriber count:
Join Revue. Select 'Hide Subscriber Count' in Account settings > Settings > Subscriber Count. Voila!
How frequently should you tweet?
1 to 20 Tweets per day, but consistency is key.
Stick to a daily tweet limit. Start with less and be consistent than the opposite.
I tweet 3 times per day. That's my comfort zone. Larger accounts tweet 5–7 times daily.
Do what works for you and that is the right amount.
Twitter is a long-term game, so plan your tweets for a year.
How to Batch Your Tweets?
Sunday batchs.
Sunday evenings take me 1.5 hours to create all my tweets for the week.
Use a word document and write down your posts. Podcasts, books, my own articles inspire me.
When I have a good idea or see a catchy Tweet, I take a screenshot.
To not copy but adapt.
Two pillars support my content:
(90% ~ 29 tweets per week) Inspirational quotes, mindfulness tips, zen stories, mistakes, myths, book recommendations, etc.
(10% 2 tweets per week) I share how I grow Mindful Monday with readers. This pillar promotes MM and behind-the-scenes content.
Second, I schedule all my Tweets using TweetDeck. I tweet at 7 a.m., 5 p.m., and 6 p.m.
Include Twitter Threads in your content strategy
Tweets are blog posts. In your first tweet, you include a headline, then tweet your content.
That’s how you create a series of connected Tweets.
What’s the point? You have more room to convince your reader you're an expert.
Add a call-to-action to your thread.
Follow for more like this
Newsletter signup (share your link)
Ask for retweet
One thread per week is my goal.
I'll schedule threads with Typefully. In the free version, you can schedule one Tweet, but that's fine.
Pin a thread to the top of your profile if it leads to your newsletter. So new readers see your highest-converting content first.
Tweet Medium posts
I also tweet Medium articles.
I schedule 1 weekly repost for 5 weeks after each publication. I share the same article daily for 5 weeks.
Every time I tweet, I include a different article quote, so even if the link is the same, the quote adds value.
Engage Other Experts
When you first create your account, few people will see it. Normal.
If you comment on other industry accounts, you can reach their large audience.
First, you need 50 to 100 followers. Here's my beginner tip.
15 minutes a day or when I have downtime, I comment on bigger accounts in my niche.
My 12-Day Results
Now let's look at the first data.
I had 32 followers on March 29. 12 followers in 11 days. I have 52 now.
Not huge, but growing rapidly.
Let's examine impressions/views.

As a newbie, I gained 4,300 impressions/views in 12 days. On Medium, I got fewer views.
The 1,6k impressions per day spike comes from a larger account I mentioned the day before. First, I was shocked to see the spike and unsure of its origin.

These results are promising given the effort required to be consistent on Twitter.
Let's see how my journey progresses. I'll keep you posted.
Tweeters, Does this content strategy make sense? What's wrong? Comment below.
Let's support each other on Twitter. Here's me.
Which Twitter strategy works for you in 2022?
This post is a summary. Read the full article here

Victoria Kurichenko
3 years ago
What Happened After I Posted an AI-Generated Post on My Website
This could cost you.

Content creators may have heard about Google's "Helpful content upgrade."
This change is another Google effort to remove low-quality, repetitive, and AI-generated content.
Why should content creators care?
Because too much content manipulates search results.
My experience includes the following.
Website admins seek high-quality guest posts from me. They send me AI-generated text after I say "yes." My readers are irrelevant. Backlinks are needed.
Companies copy high-ranking content to boost their Google rankings. Unfortunately, it's common.
What does this content offer?
Nothing.
Despite Google's updates and efforts to clean search results, webmasters create manipulative content.
As a marketer, I knew about AI-powered content generation tools. However, I've never tried them.
I use old-fashioned content creation methods to grow my website from 0 to 3,000 monthly views in one year.
Last year, I launched a niche website.
I do keyword research, analyze search intent and competitors' content, write an article, proofread it, and then optimize it.
This strategy is time-consuming.
But it yields results!
Here's proof from Google Analytics:

Proven strategies yield promising results.
To validate my assumptions and find new strategies, I run many experiments.
I tested an AI-powered content generator.
I used a tool to write this Google-optimized article about SEO for startups.
I wanted to analyze AI-generated content's Google performance.
Here are the outcomes of my test.
First, quality.
I dislike "meh" content. I expect articles to answer my questions. If not, I've wasted my time.
My essays usually include research, personal anecdotes, and what I accomplished and achieved.
AI-generated articles aren't as good because they lack individuality.
Read my AI-generated article about startup SEO to see what I mean.

It's dry and shallow, IMO.
It seems robotic.
I'd use quotes and personal experience to show how SEO for startups is different.
My article paraphrases top-ranked articles on a certain topic.
It's readable but useless. Similar articles abound online. Why read it?
AI-generated content is low-quality.
Let me show you how this content ranks on Google.
The Google Search Console report shows impressions, clicks, and average position.

Low numbers.
No one opens the 5th Google search result page to read the article. Too far!
You may say the new article will improve.
Marketing-wise, I doubt it.
This article is shorter and less comprehensive than top-ranking pages. It's unlikely to win because of this.
AI-generated content's terrible reality.
I'll compare how this content I wrote for readers and SEO performs.
Both the AI and my article are fresh, but trends are emerging.

My article's CTR and average position are higher.
I spent a week researching and producing that piece, unlike AI-generated content. My expert perspective and unique consequences make it interesting to read.
Human-made.
In summary
No content generator can duplicate a human's tone, writing style, or creativity. Artificial content is always inferior.
Not "bad," but inferior.
Demand for content production tools will rise despite Google's efforts to eradicate thin content.
Most won't spend hours producing link-building articles. Costly.
As guest and sponsored posts, artificial content will thrive.
Before accepting a new arrangement, content creators and website owners should consider this.

Jano le Roux
3 years ago
Here's What I Learned After 30 Days Analyzing Apple's Microcopy
Move people with tiny words.

Apple fanboy here.
Macs are awesome.
Their iPhones rock.
$19 cloths are great.
$999 stands are amazing.
I love Apple's microcopy even more.
It's like the marketing goddess bit into the Apple logo and blessed the world with microcopy.
I took on a 30-day micro-stalking mission.
Every time I caught myself wasting time on YouTube, I had to visit Apple’s website to learn the secrets of the marketing goddess herself.
We've learned. Golden apples are calling.
Cut the friction
Benefit-first, not commitment-first.
Brands lose customers through friction.
Most brands don't think like customers.
Brands want sales.
Brands want newsletter signups.
Here's their microcopy:
“Buy it now.”
“Sign up for our newsletter.”
Both are difficult. They ask for big commitments.
People are simple creatures. Want pleasure without commitment.
Apple nails this.
So, instead of highlighting the commitment, they highlight the benefit of the commitment.
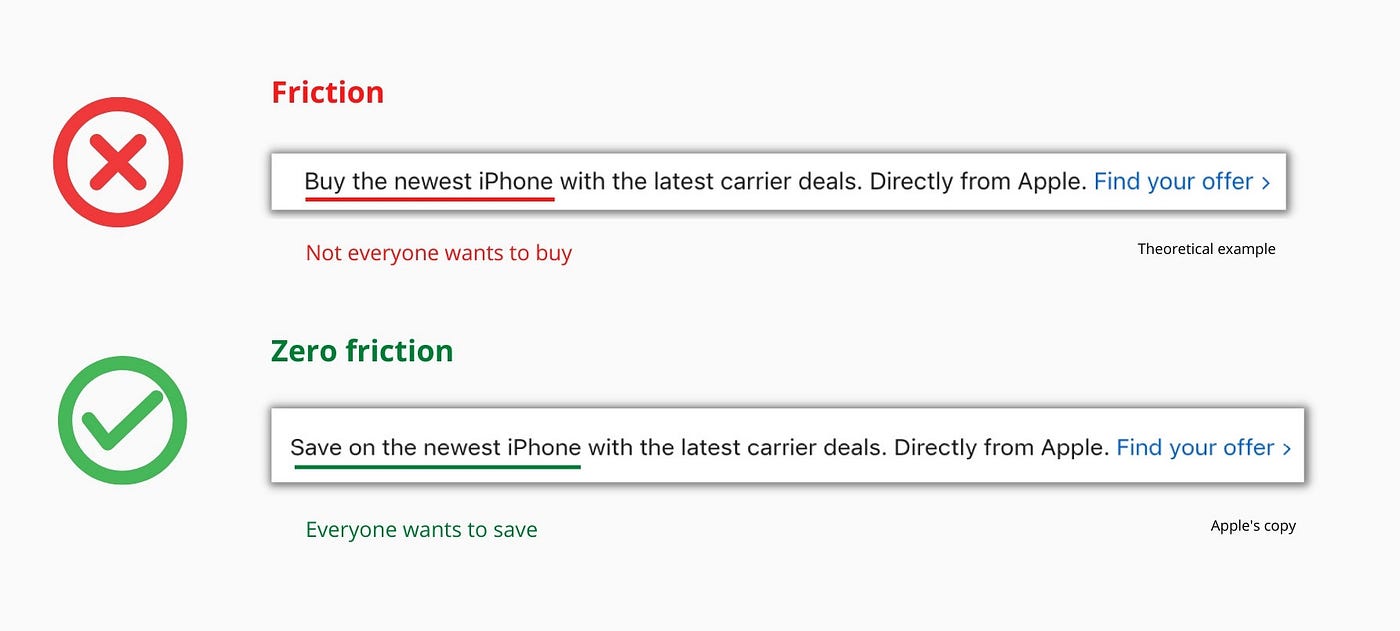
Saving on the latest iPhone sounds easier than buying it. Everyone saves, but not everyone buys.
A subtle change in framing reduces friction.
Apple eliminates customer objections to reduce friction.
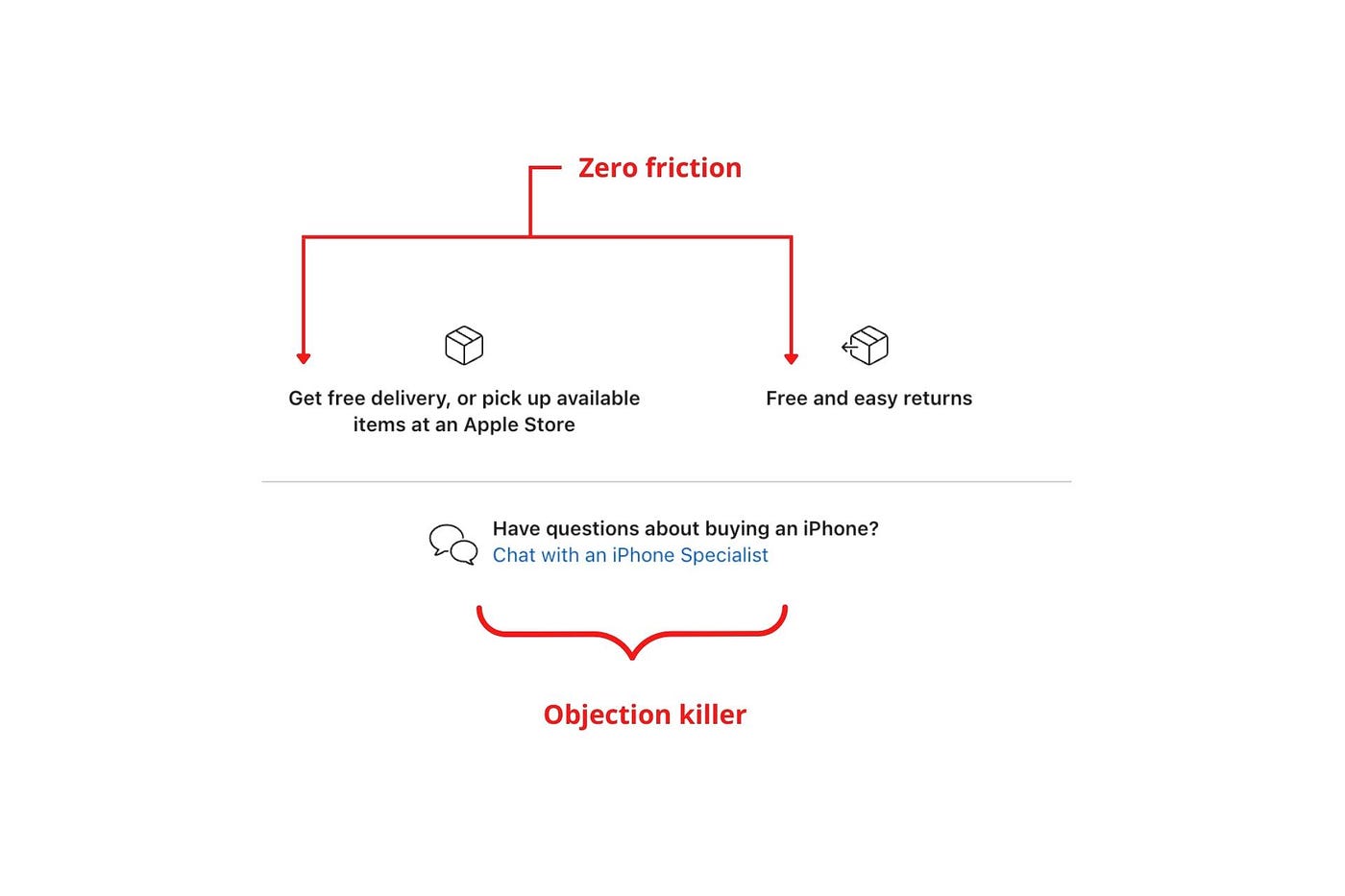
Less customer friction means simpler processes.
Apple's copy expertly reassures customers about shipping fees and not being home. Apple assures customers that returning faulty products is easy.
Apple knows that talking to a real person is the best way to reduce friction and improve their copy.
Always rhyme
Learn about fine rhyme.
Poets make things beautiful with rhyme.
Copywriters use rhyme to stand out.
Apple’s copywriters have mastered the art of corporate rhyme.
Two techniques are used.
1. Perfect rhyme
Here, rhymes are identical.

2. Imperfect rhyme
Here, rhyming sounds vary.

Apple prioritizes meaning over rhyme.
Apple never forces rhymes that don't fit.
It fits so well that the copy seems accidental.
Add alliteration
Alliteration always entertains.
Alliteration repeats initial sounds in nearby words.
Apple's copy uses alliteration like no other brand I've seen to create a rhyming effect or make the text more fun to read.
For example, in the sentence "Sam saw seven swans swimming," the initial "s" sound is repeated five times. This creates a pleasing rhythm.
Microcopy overuse is like pouring ketchup on a Michelin-star meal.
Alliteration creates a memorable phrase in copywriting. It's subtler than rhyme, and most people wouldn't notice; it simply resonates.

I love how Apple uses alliteration and contrast between "wonders" and "ease".
Assonance, or repeating vowels, isn't Apple's thing.
You ≠ Hero, Customer = Hero
Your brand shouldn't be the hero.
Because they'll be using your product or service, your customer should be the hero of your copywriting. With your help, they should feel like they can achieve their goals.
I love how Apple emphasizes what you can do with the machine in this microcopy.

It's divine how they position their tools as sidekicks to help below.

This one takes the cake:

Dialogue-style writing
Conversational copy engages.
Excellent copy Like sharing gum with a friend.
This helps build audience trust.
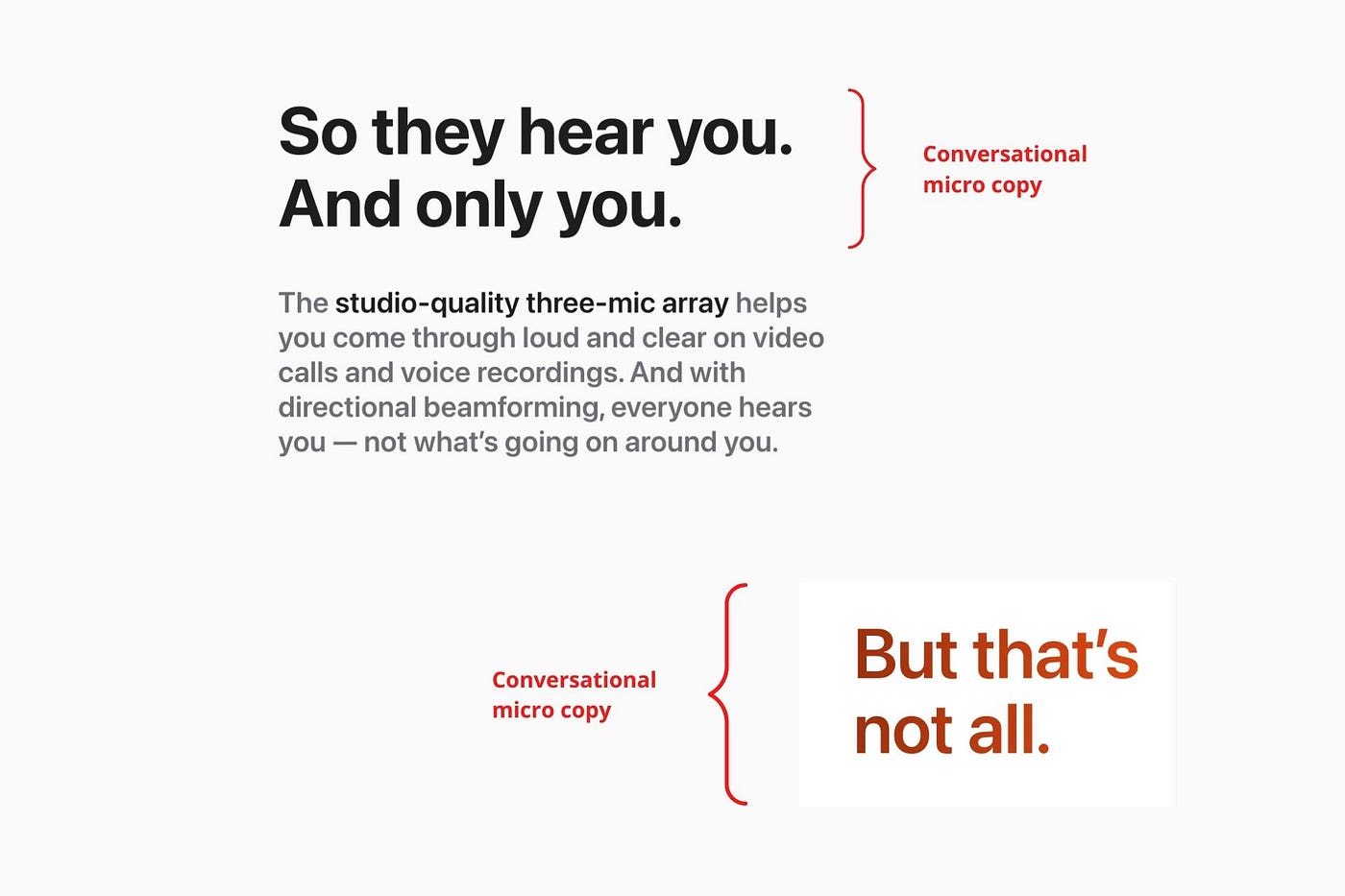
Apple does this by using natural connecting words like "so" and phrases like "But that's not all."
Snowclone-proof
The mother of all microcopy techniques.
A snowclone uses an existing phrase or sentence to create a new one. The new phrase or sentence uses the same structure but different words.
It’s usually a well know saying like:
To be or not to be.
This becomes a formula:
To _ or not to _.
Copywriters fill in the blanks with cause-related words. Example:
To click or not to click.

Apple turns "survival of the fittest" into "arrival of the fittest."
It's unexpected and surprises the reader.
So this was fun.
But my fun has just begun.
Microcopy is 21st-century poetry.
I came as an Apple fanboy.
I leave as an Apple fanatic.
Now I’m off to find an apple tree.
Cause you know how it goes.
(Apples, trees, etc.)
This post is a summary. Original post available here.
You might also like

Johnny Harris
3 years ago
The REAL Reason Putin is Invading Ukraine [video with transcript]
Transcript:
[Reporter] The Russian invasion of Ukraine.
Momentum is building for a war between Ukraine and Russia.
[Reporter] Tensions between Russia and the West
are growing rapidly.
[Reporter] President Biden considering deploying
thousands of troops to Eastern Europe.
There are now 100,000 troops
on the Eastern border of Ukraine.
Russia is setting up field hospitals on this border.
Like this is what preparation for war looks like.
A legitimate war.
Ukrainian troops are watching and waiting,
saying they are preparing for a fight.
The U.S. has ordered the families of embassy staff
to leave Ukraine.
Britain has sent all of their nonessential staff home.
And now the U.S. is sending tons of weapons and munitions
to Ukraine's army.
And we're even considering deploying
our own troops to the region.
I mean, this thing is heating up.
Meanwhile, Russia and the West have been in Geneva
and Brussels trying to talk it out,
and sort of getting nowhere.
The message is very clear.
Should Russia take further aggressive actions
against Ukraine the costs will be severe
and the consequences serious.
It's a scary, grim momentum that is unpredictable.
And the chances of miscalculation
and escalation are growing.
I want to explain what's going on here,
but I want to show you that this isn't just
typical geopolitical behavior.
Stuff that can just be explained on the map.
Instead, to understand why 100,000 troops are camped out
on Ukraine's Eastern border, ready for war,
you have to understand Russia
and how it's been cut down over the ages
from the Slavic empire that dominated this whole region
to then the Soviet Union,
which was defeated in the nineties.
And what you really have to understand here
is how that history is transposed
onto the brain of one man.
This guy, Vladimir Putin.
This is a story about regional domination
and struggles between big powers,
but really it's the story about
what Vladimir Putin really wants.
[Reporter] Russian troops moving swiftly
to take control of military bases in Crimea.
[Reporter] Russia has amassed more than 100,000 troops
and a lot of military hardware
at the border with Ukraine.
Let's dive back in.
Okay. Let's get up to speed on what's happening here.
And I'm just going to quickly give you the highlight version
of like the news that's happening,
because I want to get into the juicy part,
which is like why, the roots of all of this.
So let's go.
A few months ago, Russia started sending
more and more troops to this border.
It's this massive border between Ukraine and Russia.
They said they were doing a military exercise,
but the rest of the world was like,
"Yeah, we totally believe you Russia. Pshaw."
This was right before this big meeting
where North American and European countries
were coming together to talk about a lot
of different things, like these countries often do
in these diplomatic summits.
But soon, because of Russia's aggressive behavior
coming in and setting up 100,000 troops
on the border with Ukraine,
the entire summit turned into a whole, "WTF Russia,
what are you doing on the border of Ukraine," meeting.
Before the meeting Putin comes out and says,
"Listen, I have some demands for the West."
And everyone's like, "Okay, Russia, what are your demands?
You know, we have like, COVID19 right now.
And like, that's like surging.
So like, we don't need your like,
bluster about what your demands are."
And Putin's like, "No, here's my list of demands."
Putin's demands for the summit were this:
number one, that NATO, which is this big military alliance
between U.S., Canada, and Europe stop expanding,
meaning they don't let any new members in, okay.
So, Russia is like, "No more new members to your, like,
cool military club that I don't like.
You can't have any more members."
Number two, that NATO withdraw all of their troops
from anywhere in Eastern Europe.
Basically Putin is saying,
"I can veto any military cooperation
or troops going between countries
that have to do with Eastern Europe,
the place that used to be the Soviet Union."
Okay, and number three, Putin demands that America vow
not to protect its allies in Eastern Europe
with nuclear weapons.
"LOL," said all of the other countries,
"You're literally nuts, Vladimir Putin.
Like these are the most ridiculous demands, ever."
But there he is, Putin, with these demands.
These very, very aggressive demands.
And he sort of is implying that if his demands aren't met,
he's going to invade Ukraine.
I mean, it doesn't work like this.
This is not how international relations work.
You don't just show up and say like,
"I'm not gonna allow other countries to join your alliance
because it makes me feel uncomfortable."
But what I love about this list of demands
from Vladimir Putin for this summit
is that it gives us a clue
on what Vladimir Putin really wants.
What he's after here.
You read them closely and you can grasp his intentions.
But to grasp those intentions
you have to understand what NATO is.
and what Russia and Ukraine used to be.
(dramatic music)
Okay, so a while back I made this video
about why Russia is so damn big,
where I explain how modern day Russia started here in Kiev,
which is actually modern day Ukraine.
In other words, modern day Russia, as we know it,
has its original roots in Ukraine.
These places grew up together
and they eventually became a part
of the same mega empire called the Soviet Union.
They were deeply intertwined,
not just in their history and their culture,
but also in their economy and their politics.
So it's after World War II,
it's like the '50s, '60s, '70s, and NATO was formed,
the North Atlantic Treaty Organization.
This was a military alliance between all of these countries,
that was meant to sort of deter the Soviet Union
from expanding and taking over the world.
But as we all know, the Soviet Union,
which was Russia and all of these other countries,
collapsed in 1991.
And all of these Soviet republics,
including Ukraine, became independent,
meaning they were not now a part
of one big block of countries anymore.
But just because the border's all split up,
it doesn't mean that these cultural ties actually broke.
Like for example, the Soviet leader at the time
of the collapse of the Soviet Union, this guy, Gorbachev,
he was the son of a Ukrainian mother and a Russian father.
Like he grew up with his mother singing him
Ukrainian folk songs.
In his mind, Ukraine and Russia were like one thing.
So there was a major reluctance to accept Ukraine
as a separate thing from Russia.
In so many ways, they are one.
There was another Russian at the time
who did not accept this new division.
This young intelligence officer, Vladimir Putin,
who was starting to rise up in the ranks
of postSoviet Russia.
There's this amazing quote from 2005
where Putin is giving this stateoftheunionlike address,
where Putin declares the collapse of the Soviet Union,
quote, "The greatest catastrophe of the 20th century.
And as for the Russian people, it became a genuine tragedy.
Tens of millions of fellow citizens and countrymen
found themselves beyond the fringes of Russian territory."
Do you see how he frames this?
The Soviet Union were all one people in his mind.
And after it collapsed, all of these people
who are a part of the motherland were now outside
of the fringes or the boundaries of Russian territory.
First off, fact check.
Greatest catastrophe of the 20th century?
Like, do you remember what else happened
in the 20th century, Vladimir?
(ominous music)
Putin's worry about the collapse of this one people
starts to get way worse when the West, his enemy,
starts showing up to his neighborhood
to all these exSoviet countries that are now independent.
The West starts selling their ideology
of democracy and capitalism and inviting them
to join their military alliance called NATO.
And guess what?
These countries are totally buying it.
All these exSoviet countries are now joining NATO.
And some of them, the EU.
And Putin is hating this.
He's like not only did the Soviet Union divide
and all of these people are now outside
of the Russia motherland,
but now they're being persuaded by the West
to join their military alliance.
This is terrible news.
Over the years, this continues to happen,
while Putin himself starts to chip away
at Russian institutions, making them weaker and weaker.
He's silencing his rivals
and he's consolidating power in himself.
(triumphant music)
And in the past few years,
he's effectively silenced anyone who can challenge him;
any institution, any court,
or any political rival have all been silenced.
It's been decades since the Soviet Union fell,
but as Putin gains more power,
he still sees the region through the lens
of the old Cold War, Soviet, Slavic empire view.
He sees this region as one big block
that has been torn apart by outside forces.
"The greatest catastrophe of the 20th century."
And the worst situation of all of these,
according to Putin, is Ukraine,
which was like the gem of the Soviet Union.
There was tons of cultural heritage.
Again, Russia sort of started in Ukraine,
not to mention it was a very populous
and industrious, resourcerich place.
And over the years Ukraine has been drifting west.
It hasn't joined NATO yet, but more and more,
it's been electing proWestern presidents.
It's been flirting with membership in NATO.
It's becoming less and less attached
to the Russian heritage that Putin so adores.
And more than half of Ukrainians say
that they'd be down to join the EU.
64% of them say that it would be cool joining NATO.
But Putin can't handle this. He is in total denial.
Like an exboyfriend who handle his exgirlfriend
starting to date someone else,
Putin can't let Ukraine go.
He won't let go.
So for the past decade,
he's been trying to keep the West out
and bring Ukraine back into the motherland of Russia.
This usually takes the form of Putin sending
secret soldiers from Russia into Ukraine
to help the people in Ukraine who want to like separate
from Ukraine and join Russia.
It also takes the form of, oh yeah,
stealing entire parts of Ukraine for Russia.
Russian troops moving swiftly to take control
of military bases in Crimea.
Like in 2014, Putin just did this.
To what America is officially calling
a Russian invasion of Ukraine.
He went down and just snatched this bit of Ukraine
and folded it into Russia.
So you're starting to see what's going on here.
Putin's life's work is to salvage what he calls
the greatest catastrophe of the 20th century,
the division and the separation
of the Soviet republics from Russia.
So let's get to present day. It's 2022.
Putin is at it again.
And honestly, if you really want to understand
the mind of Vladimir Putin and his whole view on this,
you have to read this.
"On the History of Unity of Russians and Ukrainians,"
by Vladimir Putin.
A blog post that kind of sounds
like a ninth grade history essay.
In this essay, Vladimir Putin argues
that Russia and Ukraine are one people.
He calls them essentially the same historical
and spiritual space.
Kind of beautiful writing, honestly.
Anyway, he argues that the division
between the two countries is due to quote,
"a deliberate effort by those forces
that have always sought to undermine our unity."
And that the formula they use, these outside forces,
is a classic one: divide and rule.
And then he launches into this super indepth,
like 10page argument, as to every single historical beat
of Ukraine and Russia's history
to make this argument that like,
this is one people and the division is totally because
of outside powers, i.e. the West.
Okay, but listen, there's this moment
at the end of the post,
that actually kind of hit me in a big way.
He says this, "Just have a look at Austria and Germany,
or the U.S. and Canada, how they live next to each other.
Close in ethnic composition, culture,
and in fact, sharing one language,
they remain sovereign states with their own interests,
with their own foreign policy.
But this does not prevent them
from the closest integration or allied relations.
They have very conditional, transparent borders.
And when crossing them citizens feel at home.
They create families, study, work, do business.
Incidentally, so do millions of those born in Ukraine
who now live in Russia.
We see them as our own close people."
I mean, listen, like,
I'm not in support of what Putin is doing,
but like that, it's like a pretty solid like analogy.
If China suddenly showed up and started like
coaxing Canada into being a part of its alliance,
I would be a little bit like, "What's going on here?"
That's what Putin feels.
And so I kind of get what he means there.
There's a deep heritage and connection between these people.
And he's seen that falter and dissolve
and he doesn't like it.
He clearly genuinely feels a brotherhood
and this deep heritage connection
with the people of Ukraine.
Okay, okay, okay, okay. Putin, I get it.
Your essay is compelling there at the end.
You're clearly very smart and wellread.
But this does not justify what you've been up to. Okay?
It doesn't justify sending 100,000 troops to the border
or sending cyber soldiers to sabotage
the Ukrainian government, or annexing territory,
fueling a conflict that has killed
tens of thousands of people in Eastern Ukraine.
No. Okay.
No matter how much affection you feel for Ukrainian heritage
and its connection to Russia, this is not okay.
Again, it's like the boyfriend
who genuinely loves his girlfriend.
They had a great relationship,
but they broke up and she's free to see whomever she wants.
But Putin is not ready to let go.
[Man In Blue Shirt] What the hell's wrong with you?
I love you, Jessica.
What the hell is wrong with you?
Dude, don't fucking touch me.
I love you. Worldstar!
What is wrong with you? Just stop!
Putin has constructed his own reality here.
One in which Ukraine is actually being controlled
by shadowy Western forces
who are holding the people of Ukraine hostage.
And if that he invades, it will be a swift victory
because Ukrainians will accept him with open arms.
The great liberator.
(triumphant music)
Like, this guy's a total romantic.
He's a history buff and a romantic.
And he has a hill to die on here.
And it is liberating the people
who have been taken from the Russian motherland.
Kind of like the abusive boyfriend, who's like,
"She actually really loves me,
but it's her annoying friends
who were planting all these ideas in her head.
That's why she broke up with me."
And it's like, "No, dude, she's over you."
[Man In Blue Shirt] What the hell is wrong with you?
I love you, Jessica.
I mean, maybe this video should be called
Putin is just like your abusive exboyfriend.
[Man In Blue Shirt] What the hell is wrong with you?
I love you, Jessica!
Worldstar! What's wrong with you?
Okay. So where does this leave us?
It's 2022, Putin is showing up to these meetings in Europe
to tell them where he stands.
He says, "NATO, you cannot expand anymore. No new members.
And you need to withdraw all your troops
from Eastern Europe, my neighborhood."
He knows these demands will never be accepted
because they're ludicrous.
But what he's doing is showing a false effort to say,
"Well, we tried to negotiate with the West,
but they didn't want to."
Hence giving a little bit more justification
to a Russian invasion.
So will Russia invade? Is there war coming?
Maybe; it's impossible to know
because it's all inside of the head of this guy.
But, if I were to make the best argument
that war is not coming tomorrow,
I would look at a few things.
Number one, war in Ukraine would be incredibly costly
for Vladimir Putin.
Russia has a far superior army to Ukraine's,
but still, Ukraine has a very good army
that is supported by the West
and would give Putin a pretty bad bloody nose
in any invasion.
Controlling territory in Ukraine would be very hard.
Ukraine is a giant country.
They would fight back and it would be very hard
to actually conquer and take over territory.
Another major point here is that if Russia invades Ukraine,
this gives NATO new purpose.
If you remember, NATO was created because of the Cold War,
because the Soviet Union was big and nuclear powered.
Once the Soviet Union fell,
NATO sort of has been looking for a new purpose
over the past couple of decades.
If Russia invades Ukraine,
NATO suddenly has a brand new purpose to unite
and to invest in becoming more powerful than ever.
Putin knows that.
And it would be very bad news for him if that happened.
But most importantly, perhaps the easiest clue
for me to believe that war isn't coming tomorrow
is the Russian propaganda machine
is not preparing the Russian people for an invasion.
In 2014, when Russia was about to invade
and take over Crimea, this part of Ukraine,
there was a barrage of state propaganda
that prepared the Russian people
that this was a justified attack.
So when it happened, it wasn't a surprise
and it felt very normal.
That isn't happening right now in Russia.
At least for now. It may start happening tomorrow.
But for now, I think Putin is showing up to the border,
flexing his muscles and showing the West that he is earnest.
I'm not sure that he's going to invade tomorrow,
but he very well could.
I mean, read the guy's blog post
and you'll realize that he is a romantic about this.
He is incredibly idealistic about the glory days
of the Slavic empires, and he wants to get it back.
So there is dangerous momentum towards war.
And the way war works is even a small little, like, fight,
can turn into the other guy
doing something bigger and crazier.
And then the other person has to respond
with something a little bit bigger.
That's called escalation.
And there's not really a ceiling
to how much that momentum can spin out of control.
That is why it's so scary when two nuclear countries
go to war with each other,
because there's kind of no ceiling.
So yeah, it's dangerous. This is scary.
I'm not sure what happens next here,
but the best we can do is keep an eye on this.
At least for now, we better understand
what Putin really wants out of all of this.
Thanks for watching.

Jayden Levitt
3 years ago
How to Explain NFTs to Your Grandmother, in Simple Terms

In simple terms, you probably don’t.
But try. Grandma didn't grow up with Facebook, but she eventually joined.
Perhaps the fear of being isolated outweighed the discomfort of learning the technology.
Grandmas are Facebook likers, sharers, and commenters.
There’s no stopping her.
Not even NFTs. Web3 is currently very complex.
It's difficult to explain what NFTs are, how they work, and why we might use them.
Three explanations.
1. Everything will be ours to own, both physically and digitally.
Why own something you can't touch? What's the point?
Blockchain technology proves digital ownership.
Untouchables need ownership proof. What?
Digital assets reduce friction, save time, and are better for the environment than physical goods.
Many valuable things are intangible. Feeling like your favorite brands. You'll pay obscene prices for clothing that costs pennies.
Secondly, NFTs Are Contracts. Agreements Have Value.
Blockchain technology will replace all contracts and intermediaries.
Every insurance contract, deed, marriage certificate, work contract, plane ticket, concert ticket, or sports event is likely an NFT.
We all have public wallets, like Grandma's Facebook page.
3. Your NFT Purchases Will Be Visible To Everyone.
Everyone can see your public wallet. What you buy says more about you than what you post online.
NFTs issued double as marketing collateral when seen on social media.
While I doubt Grandma knows who Snoop Dog is, imagine him or another famous person holding your NFT in his public wallet and the attention that could bring to you, your company, or brand.
This Technical Section Is For You
The NFT is a contract; its founders can add value through access, events, tuition, and possibly royalties.
Imagine Elon Musk releasing an NFT to his network. Or yearly business consultations for three years.
Christ-alive.
It's worth millions.
These determine their value.
No unsuspecting schmuck willing to buy your hot potato at zero. That's the trend, though.
Overpriced NFTs for low-effort projects created a bubble that has burst.
During a market bubble, you can make money by buying overvalued assets and selling them later for a profit, according to the Greater Fool Theory.
People are struggling. Some are ruined by collateralized loans and the gold rush.
Finances are ruined.
It's uncomfortable.
The same happened in 2018, during the ICO crash or in 1999/2000 when the dot com bubble burst. But the underlying technology hasn’t gone away.

Bloomberg
3 years ago
Expulsion of ten million Ukrainians
According to recent data from two UN agencies, ten million Ukrainians have been displaced.
The International Organization for Migration (IOM) estimates nearly 6.5 million Ukrainians have relocated. Most have fled the war zones around Kyiv and eastern Ukraine, including Dnipro, Zhaporizhzhia, and Kharkiv. Most IDPs have fled to western and central Ukraine.
Since Russia invaded on Feb. 24, 3.6 million people have crossed the border to seek refuge in neighboring countries, according to the latest UN data. While most refugees have fled to Poland and Romania, many have entered Russia.
Internally displaced figures are IOM estimates as of March 19, based on 2,000 telephone interviews with Ukrainians aged 18 and older conducted between March 9-16. The UNHCR compiled the figures for refugees to neighboring countries on March 21 based on official border crossing data and its own estimates. The UNHCR's top-line total is lower than the country totals because Romania and Moldova totals include people crossing between the two countries.
Sources: IOM, UNHCR
According to IOM estimates based on telephone interviews with a representative sample of internally displaced Ukrainians, over 53% of those displaced are women, and over 60% of displaced households have children.
